Phishing Awareness Toolkit
Materials in this toolkit are available to the entire UC community. Items marked "Grab-and-go" are intended to be quick and easy to use or customize (e.g. substituting a local URL and/or logo for the systemwide one provided). Additional materials are also provided for those looking for a wider variety from which to choose or modify.
For editable files beyond what is available here, please contact your Systemwide Information Security Awareness Workgroup rep(s), listed to the left. If your location isn't listed, please email Cecelia Finney at cecelia.finney@ucop.edu.
| Article | Posters | Videos | Quizzes | Informational Web Pages | Newsletters | Social Media Posts | Webinar |
Article: "Don't Let a Phishing Scam Reel You In". "Grab-and-go"
Cybercriminals use phishing—a type of social engineering—to manipulate people into doing what they want. Technology makes phishing easy. Setting up and operating a phishing attack is fast, inexpensive, and low risk: any cybercriminal with an e-mail address can launch one. Students, staff, and faculty have all suffered losses from phishing. Knowing what you're up against can help you be more secure. Here are a few things you can do to guard against phishing attacks... [More... See the full article]
Posters:
Click on thumbnail for full size flyer.
"Grab-and-go" Posters:
Note: Shark-and-penguin "Grab-and'go" posters have a customizable footer only. More flexible versions are available but require additional time/effort to customize.
 |
 |
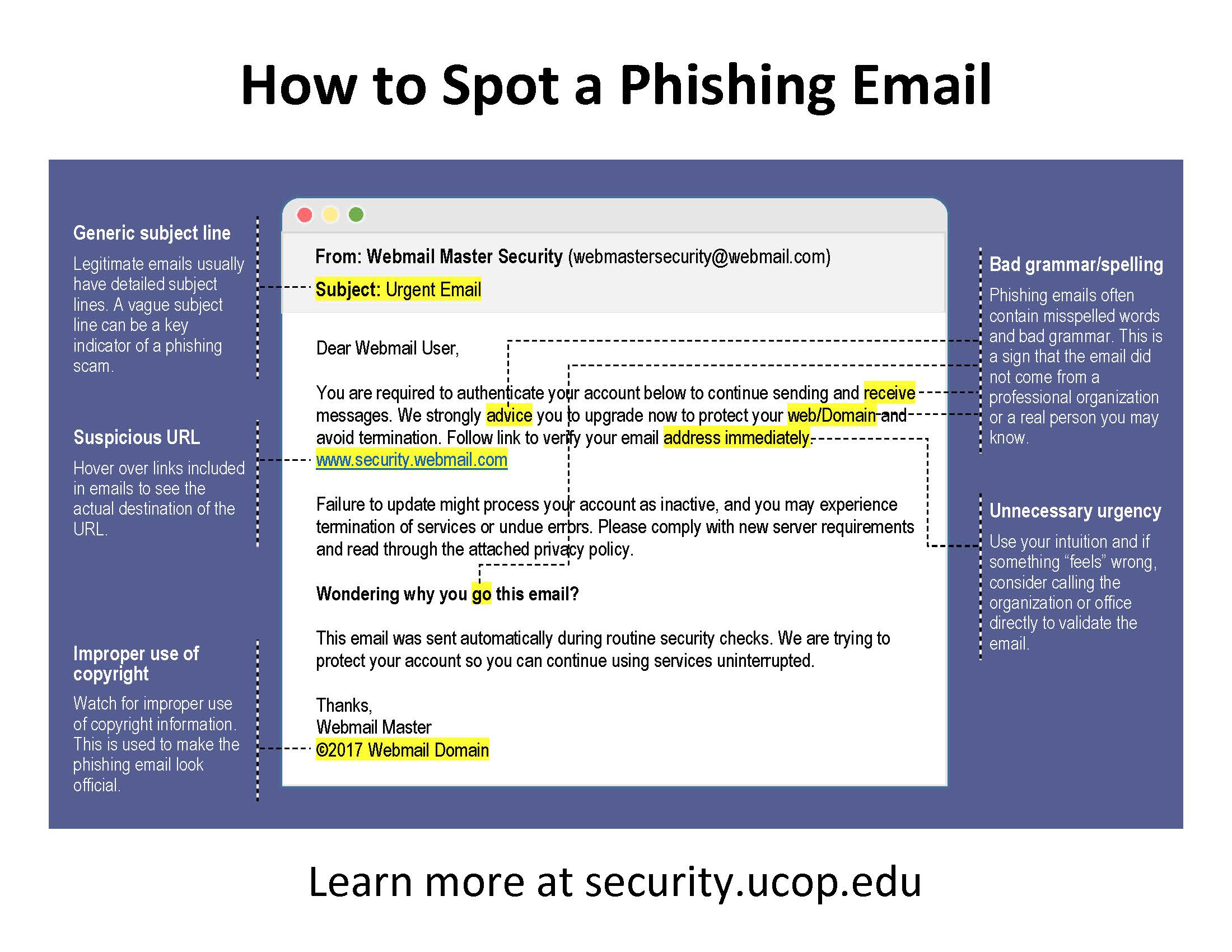
*Best for online or presentation use. |
Additional Posters:
 |
 |
Videos: (all closed captioned)
"Grab-and-go" Videos:
- Phishing/General Protection (STOP. THINK. CONNECT.) (1:16 min)
- Some good tips that aren’t included in other videos, like how easy it is to replicate an organization's image/logo. Short and easy to follow.
- RBC Cyber Security - No Phishing! (Royal Bank of Canada) (2:15 min)
- Humorous, well done video. A take on Norse mythology and gaming. Friends helping friends recognize what to do. Mentions the ‘s’ in https and how criminals are getting good at faking it. Highlights two common phishes.
- Protect Yourself from Phishing Attacks (UCSB) (0:55 sec)
- Mirrors the main points from the above article.
Additional Videos:
- “Phishing E-Safe” (Univ of Michigan, 2013) (1:02 min)
- Shows a real individual and her story. Convincing and engaging. From higher ed institution. Good for students.
- What does Phishing mean? (Decoded (a technology company)) (1:12 min)
- Very short, fast audio, but lots of good information. For example, how phishing can lead to stealing confidential information at your company. Mentions password managers and two factor authentication. Could be effective for students.
- "Hang Up on Phone Fraud" (Federal Trade Commission) (3:08 min)
- Examples of actual scams, including someone clicking on a link in email.
- At just over 3 minutes, this video is a good candidate for an easy, short, view-and-discuss session.
- Note: Points to FTC reporting channels and URLs.
- "Hang Up on Fraudulent Telemarketing" (FTC) (3:07 min)
- Examples of actual scams. Second half (what to do) is the same as second half of "Hang Up on Phone Fraud" above. Same notes apply, though different examples are used.
- Examples of actual scams. Second half (what to do) is the same as second half of "Hang Up on Phone Fraud" above. Same notes apply, though different examples are used.
Quizzes:
"Grab-and-go" Quiz:
- OpenDNS Phishing Quiz. Nice phishing quiz with examples of safe vs. phishy URLs
Additional Quizzes:
- FTC (Federal Trade Commission) phishing scams game. 5 question quiz. Well done; helpful information. Also available for download (click "Downloads" tab below the quiz).
- Note: Promotes FTC reporting channels and URLs. Take this into consideration when choosing whether to use.
- SonicWALL Phishing and Spam IQ Quiz. Fun, informative quiz to test how well you distinguish between email schemes and legitimate email. A little sales pitchy at the very end.
Informational Web Pages:
"Grab-and-go" Web Pages:
- UCSD Phishing Guide: How To Identify Phishing Scams
- US-CERT: Avoiding Social Engineering and Phishing Attacks
- Consumer information about phishing from the Federal Trade Commission (FTC)
Additional Web Pages:
- UCSC “Beware of Scams” page
- UCLA "Phish Bowl" - examples of email phishing scams
- UCOP “Prevent Emails from Looking Phishy” page
Newsletters:
"Grab-and-go" Newsletter:
SANS OUCH Newsletter on social engineering (from Jan 2017 but still "current")
Additional Newsletters:
SANS OUCH Newsletter: "Stop That Phish" (April 2018)
MS-ISAC/CIS newsletter: Identifying and Reporting Common Scams (July 2017)
Social Media Posts:
"Grab-and-go" Posts:
- Never email confidential information to anyone. #Phishing
- Hover to discover: Mouse over links in email to reveal their true URL. Avoid getting phished—no hook for you! #Phishing #CyberAware
- “Verify your account by midnight or it will turn into a pumpkin!” Get a message urging you to take action? Delete it! #Phishing #CyberAware
- Receive a suspicious email from a friend or colleague? Call them to ask if they really sent it. #Phishing #CyberAware
Additional Posts:
- #Phishing attacks: Report phishy communications to your IT department.
- Reputable institutions will never email you to confirm details of your account. #Phishing
- Typos or other mistakes may indicate the email in question is a #Phishing attack.
- Never give out information over the phone if you did not initiate the call. #Phishing
- Be wary of links emailed or texted from unknown or unverified senders. Type the URL in your browser. #Phishing
- Hover over links in messages to see where they truly lead. Better yet, type a known URL into your browser. #Phishing #CyberAware
- Afraid you’ve fallen for a #phishing scam? Stop what you’re doing & change your password immediately! Then notify the Help Desk. #CyberAware
- Posting personal information or travel details publicly provides fuel for scam artists. #Phishing #CyberAware #PrivacyAware
- Manage your social media carefully: Posting personal info online creates bait for scams and #phishing. #CyberAware #PrivacyAware
- Email attachments: A cybercriminal's #1 choice for spreading malicious software. Do not open unexpected attachments! #Phishing #CyberAware
- Trust your instincts: Does that message feel off? It probably is. Contact the sender to confirm it's legit. #Phishing #CyberAware
- Is it urgent? Slow down. Cybercriminals want you to do what you're told, when you're told. Think before you click. #Phishing #CyberAware
- Remember: #Phishing is not just for email! You can get phished by phone, text message, on social media, or in person. #CyberAware
Webinars
"Grab-and-go" Webinar:
Too Legit to Quit: How to Avoid Making Legitimate Campus Messages Look Phishy - An Educause/HEISC Webinar
Speakers: Petr Brym (UC Davis), Patricia Clay (DeSales University), and Ed Hudson (CSU, Office of the Chancellor)
(Live webinar event recorded on February 21, 2018.)
Description: With phishing attacks becoming more sophisticated and increasingly successful, we can’t simply rely on educating end users. How do we avoid making legitimate campus messages look phishy? How do we keep email a reliable channel for campus communications? And what are the tools or methods available to supplement our anti-phishing training campaigns on campus? This webinar will offer lessons learned, as well as the pros and cons of viable strategies for creating well-crafted messages that look legitimate. Attendees will be encouraged to share effective communication approaches they’ve used to successfully supplement a phishing awareness campaign on their campus.
Additional webinar:
Phishing Programs: Chapter 1 – Getting Your Campus Ready for a Phishing Awareness Campaign - April 2017
---
