Guidelines and Strategies

Volunteers for the Data Disposal Day gather beside some of the many items ready for safe disposal.
"It’s easy to forget what sensitive information might be on an old hard drive or document. Proper disposal is crucial to protect you, your family, and the university from data breaches."
—Josh Drummond, CISO, UC Irvine
One of the most anticipated events of the year at UC Irvine is Data Disposal Day, a dedicated initiative for the secure disposal of paper and electronic data devices. This year, hundreds of community members from across the campus participated, bringing in used boxes of documents and electronic media to be sorted and securely destroyed. “Data Disposal Day is an extremely popular event,” shared Josh Drummond, UC Irvine’s Chief Information Security Officer (CISO). “We get requests to do it again just weeks after the event.”
Disposing of institutional information requires careful handling to prevent unauthorized access or accidental disclosure of sensitive data, which bad actors could exploit. The UC Institutional Information Disposal Standard offers guidance on how to properly dispose of data based on its risk level, from very low-risk data (P1) to very high-risk data (P4). For example, a thumb drive containing P1 data can simply be deleted, while one containing P4 data must be securely erased or destroyed. Additionally, this process must align with the UC University Records Management Program (BFBRMP-1) and the UC Records Retention Schedule.
2024 Data Disposal Day by the Numbers
- 18,000+ pounds of shredded paper, almost filling 2 large trucks
- 1,790+ hard drives destroyed
- 860+ other media (phones, tablets, floppy disks, CDs, and various other data storage gadgets) destroyed

The intersection of governance and compliance, driven by emerging standards and external factors, poses significant challenges for our tools and systems. Our policies will continually adapt to meet these evolving requirements.
Compliance: Graham-Leach-Bliley Act
The Graham-Leach-Bliley Act (GLBA) exemplifies the intersection of compliance and governance. GLBA requires institutions that offer consumers financial products or services like loans, financial or investment advice, or insurance to explain their information-sharing practices to their customers and safeguard sensitive data. One of the requirements calls for a written report of an information security program.
GLBA Survey and Report Update: To fulfill the requirement of a written report, a survey was created for the UC locations, which was completed in 2023 and updated in 2024. The survey included existing implementations that meet GLBA requirements, as well as areas for improvement. Based on the results, reports containing the full picture of GLBA compliance across UC locations were developed.
UC Location Plans for GLBA Compliance: To meet obligations under GLBA, UC locations developed compliance plans. For example, UC Berkeley’s plan includes a custom-built risk registry and action plans for impacted systems.
Resource Updates
In the spirit of continuous improvement, the following documents were revised based on tabletop exercises in 2022 and 2023, as well as feedback from multiple stakeholders in the process.
Systemwide Cyber Incident Response Process: This document defines the systemwide cyber incident response coordination process at UC.
Cyber Incident Escalation Protocol and Guidance: The document provides revised guidance on implementing the Cyber Incident Escalation Protocol.
In partnership with the entire campus community, the Information Security Office (ISO) at UC Berkeley completed a 4.5-year initiative to integrate all central IT, academic, and administrative units into the campus IS-3 cyber risk management program. UC Berkeley’s Cyber Risk Management Program is a holistic program that helps units manage their cyber risk and comply with IS-3, UC’s systemwide Electronic Information Security Policy.
This project was focused on raising awareness among Unit Heads and Unit Information Security Leads (UISLs) about their roles and responsibilities related to information security and providing units with concrete, unitspecific, prioritized recommendations on how to address areas of highest risk. Throughout the project, the emphasis was on risk awareness and risk management, providing value to the unit, building relationships, and incremental progress over time. Onboarding started in 2020, and the final cohort wrapped up in 2024. The team shared the work at the annual UC Tech Conference in a presentation entitled UC Berkeley’s IS-3 Risk Assessment Journey.
Key Program Principles
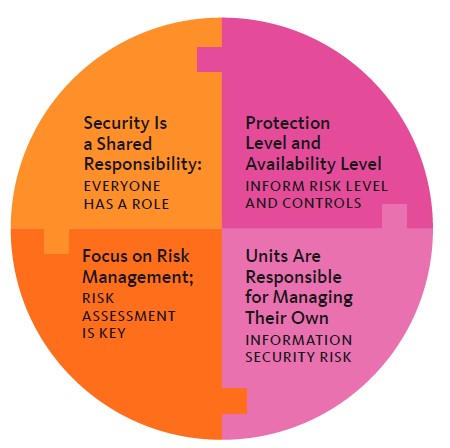
Outcomes
- ISO identified 84 academic and administrative units, met with every Unit Head and UISL, and worked in cohorts through a facilitated process of asset inventory and high-level security self-assessment.
- The units completed, and ISO reviewed, a total of 95 unit self-assessments.
2025 Next Steps
In 2025, this project will transition to an ongoing, operational program of regular reviews and updates, continuing to focus on addressing areas of highest risk; measurable, incremental improvement over time; and maintaining relationships. The operational program will also include an annual theme that focuses on a key risk area relating to IS-3. These themes will provide information, resources, and tools, such as services and templates, to help units make progress in the focus area. Over time, ISO envisions having a robust suite of tools and services to help units manage their information security risk.